Comment
Venture Sciences In Actu! – A Visit at the EAB Research Projects Conference (EAB-RPC) 2016
Special thanks to the Rosa-Luxemburg-Stiftung for making this research possible.
Up to now, knowledge about societal contexts in which border technologies are being developed, have rarely been examined as part of a critical border-regime-analysis. The present contribution can therefore be regarded as a praxeological approach to a comparatively new field of study. It consists of an ethnographic sketch, focussing on research and development of biometric applications as part of ongoing research to smart border solutions in Europe. The aim is to conflate migration and border studies with science and technology studies, so as to investigate the development of digital borders in Europe. Contrary to Helle Sternum’s text about European databases for migration control, most projects presented and discussed at the annual EAB Research Projects Conference this year did not concentrate on migration, but thematically covered travellers and beneficiaries to mobility. It is only from a broader perspective that the biometric solutions to border management, which were at the core of the conference, can communicate to the knowledge-societal contexts of migration, such as migration control, but also controlling the population on European territory and their privacy interests, and not least including the infrapolitics and dissidences of transit-migrants. Therefore, the following sketch represents a mere episode within a whole arrangement of contexts, which I have identified as information and control continuums, in relation to the techno-social formations of the European Border.1Cp. Brigitta Kuster and Vassilis Tsianos, “How to Liquefy a Body on the Move: Eurodac and the Making of the European Digital Border”, in: Raphael Bossong and Helena Carrapico (eds.), EU Borders and Shifting Internal Security. Technology, Externalization and Accountability, Heidelberg, Springer International Publishing, 2016, pp. 45–63.
I.
Growth impulses and security requirements – late August 2016 sees Angela Merkel touring through Europe. She is armed with a Franco-German action pack on security, migration management and terror defense (title: “A contribution to heighten internal security in Europe”2“Ein Beitrag zur Erhöhung der inneren Sicherheit in Europa” (transl. S.M.).). Amongst other things, she is advocating for standardized European identity management strategies, for more cross-border collaborations or, to be precise, for enhanced networks and the development of existing border and security systems. The four-page long paper, signed off by de Mazière and Cazeneuve, states:
“This year we must strike a political agreement regarding the cornerstones of an Entry-Exit-System (EES) and we should consider the inclusion of EU-citizens. Furthermore, this year requires for us to settle on the establishment of a European travel information and authorisation system (ETIAS).”3“Dieses Jahr müssen wir zu einer politischen Einigung über die Eckpunkte eines Ein- und Ausreiseregisters (Entry-Exit-System, EES) kommen und wir sollten eine Einbeziehung von EU-Bürgern prüfen. Wir brauchen zudem noch in diesem Jahr eine Einigung über die Einrichtung eines Europäischen Reiseinformations- und Genehmigungssystems (ETIAS).” (transl. S.M.)
What migration studies are investigating under the technical terminus of a “security-migration-nexus”, seems to have become almost natural law in European politics. Border security and counterterrorism are named in one breath. Connecting European security agencies, developing data-infrastructures for border security and collecting information on travellers seem to respond to the need of the hour. Managing the mobility and residency of humans through their identities is a form of governance, which does not necessarily guarantee nationally awarded human rights, as David Lyon, sociologist and director of the surveillance studies centre at Queens University in Kingston (Ontario), points out.4Cp. David Lyon, “Identification, colonialism, and control: surveillant sorting in Israel/Palestine”, in: Elia Zureik, David Lyon and Yasmeen Abu-Laban (eds.), Surveillance and Control in Israel/Palestine. Population, Territory and Power, London/New York, Routledge, 2011, pp. 49–64. Conversely, it seems relevant to note that biometric technologies continue to be deemed the largest growing market in Europe, increasingly expanding onto the African continent. At stake are the various utilizations of data patterns, which relate to the singular body features of every human being. At present, the focus lies particularly on exploring areas such as multi-biometry, the combination of a number of biometric features, such as fingerprint and iris, but also behavioural biometrics, vein recognition or contactless biometrics, as well as mobile applications.
The securization of discourses on migration is paralleled by the militarisation and technologisation of border controls, whereas border security and border management rely increasingly on markets for electronic border protection facilities,5Examples for this include the Sistema Integrado de Vigilancia Exterior, the integrated electronic system for outdoor surveillance SIVE in Spain, or the EU-wide border surveillance system called EUROSUR. as well as for virtual or intelligent borders: Tracking is the main paradigm of contemporary border security, where technologies such as biometrics, thermographic cameras and other sensor-technologies, radars and drones are employed. This leads to some authors referring to a “EU security-industrial complex”6Ben Hayes, NeoConOpticon –The EU Security-Industrial Complex, Transnational Institute in association with Statewatch, 2009. Available at: http://www.statewatch.org/analyses/neoconopticon-report.pdf [accessed May 30, 2017].. A complex, which assures “internal security” to also be executed through the external EU borders, and addresses the relationship between military and police actors, security agencies, governments and the mostly transnational industries of advanced technology, security and defence (important European players are e.g. the Thales Group, Finmeccanica, Sagem, Accenture and Morpho, both part of Safran S.A., Airbus Group, Indra Sistemas S.A., BAE Systems and last but not least Siemens), which operate within the global border security technology market. This networked security-industrial-complex horizontally connects political and private enterprise elites throughout Europe.
At the level of security policies, the entangled processes of institutionalisation of politics and economy have already largely been conflated. Bastiaan van Apeldoorn and Laura Horn describe these reciprocal integrations and entanglements as a process of “marketization of European corporate control”7Bastiaan van Apeldoorn and Laura Horn, “The Marketisation of European Corporate Control: A Critical Political Economy Perspective”, New Political Economy, 12(2), 2007, pp. 211–235. According to these authors, the process of European integration, which has been driven by a project of neoliberal marketization since the late 1980s, has played a leading role in the emergence of European shareholder capitalism. Entering new markets is important in terms of the competition European industries … Continue reading, which implies a social and political constitution of markets. However, it seems important to also consider those new forms of politics especially present in the area of border management, which is increasingly mediated by expanding agencies and their projects, operations (e.g. Mare Nostrum or the Frontex-Operation Triton respectively), missions (e.g. EUNAVFOR Med to supress trafficking networks) or programs.8The authors of a paper published by the German Institute for International and Security Affairs, SWP titled “Border Security, Camps, Quotas: The Future of European Refugee Policy?” highlight that Frontex has ten times as many employees as when the agency was founded, while their annual budget has risen from six to 245 million Euros. Cp. Steffen Angenendt, David Kipp and Anne Koch, “Border Security, Camps, Quotas: The Future of European Refugee Policy?”, SWP Comments 2016/C 32, June … Continue reading Formally assigned to technical, economic and administrative tasks, agencies like Frontex or eu-LISA increasingly direct their working structure towards networks and partners from within the private sector.9Frontex for example made headlines on the 27th and 28th of January 2016 through a pitch on Lesbos. Securiport LLC, Crossmatch, Unisys, Thales and 3M were invited to present suggestions for a design of smartphone apps and databases to track refugees arriving in Europe. For a more detailed discussion see: Diane Taylor and Emma Graham-Harrison, “EU asks tech firms to pitch refugee-tracking systems”, in The Guardian, February 18, 2016. Available at: … Continue reading
Technoscience & Venture Science
The analytical concept of technoscience describes a dispositif, in which science appears as cosmoplastic, expedited and constituted through technologies and their instruments/devices. Science creates technofacts. In addition to this concept, the role of science and research can be considered as Venture Science. Kaushik Sunder Rajan coins this terminology through his research on the symbiosis of venture capital and biotechnology.10Cp. Kaushik Sunder Rajan, Biokapitalismus. Werte im postgenomischen Zeitalter, Frankfurt a. M., Suhrkamp, 2009, p. 122. It is meant to emphasize the futurity, the hype and the promise of a scientific knowledge production – including the contingency of whether or not a certain prediction will apply. Venture Science Capitalism, or the projects ascribing to this prognostic type of knowledge, do not require fundamental research in a traditional sense. As knowledge is ‘produced’ directly by corporations, knowledge bases generate themselves straight from a user perspective. This is of vital importance for critical corporate control, or for technological impact assessment informed by social sciences. For if science is user generated instead of user oriented, the boundaries between provider and user or consumer blur and become impulsive factors of knowledge production – such is the case here with security research by governmental or EU-institutions. Venture Science creates technofacts through research financed collectively by the public sector, private investors and large industrial syndicates.11Central to this, especially when considered as switch points or points of intersections of the EU-network between the private sector and the EU-administration, as well as the legislative, are above all the EU research framework programmes, such as Horizon 2020, which concern the “research and innovation” programmes. For example, the Seventh Framework Programme FP7, initiated in 2007, focuses heavily on security. The commission has provided the programme with 1,4 billion Euros with a … Continue reading
II.
In Darmstadt, directly opposite the research and congress centrum Darmstadtium, the Fraunhofer IGD12The Fraunhofer IGD (Institute for graphic data processing) broadly speaking engages with the problems and possibilities in operating with computer data within hard- and software. Founded in 1992, it upholds a total of twelve research and development divisions located in Darmstadt, Rostock, Graz and Singapur, which work closely with the respective technical universities, as well as with clients and partners from industrial and economic sectors. The Fraunhofer IGD is internationally recognized as … Continue reading is situated in immediate proximity of the technical university. This is the site for the European Association for Biometrics (EAB) to organize a two-day conference, taking place in September 2016, the EAB Research Projects Conference 2016. The EAB is listed as a non-profit organisation whose aim is to advance the use of biometrics in Europe, taking into account the interests of European citizens, industry, academia and governments. The conference – this being the third of its kind – serves to present research results within areas of border control, speaker verification and “template protection” – a procedure to secure characteristic data within biometric person recognition – and discuss the benefits “for our European societies”. The goal of EAB-RPC 2016 was to present and discuss all larger European research projects on biometrics and identity management. In the conference announcement it reads as follows:
“This will contribute to a stronger research community at European level and a stronger position for European R&D in an international context.”
The main topic of 2016 was “identity management” at borders. Within the European Union, this still primarily means a focus on external borders, which naturally includes migration, but also goes beyond. Currently, identity management primarily looks for innovative solutions for safe and secure biometrics according to data protection requirements, as for example in a federated ID management (FidM), where the respective information remains at its exact location and can be shared on demand, instead of collecting it in a large centralized database, which would be more prone to attacks. This is a contradiction to tendencies of centralization, as within eu-LISA managed databases, which are picked up on later, at the conference’s conclusion.
The conference kicked off with Alexander Nouak, CEO of the Fraunhofer IGD and president of the EAB, who provides insight into the history of the organisation. He is followed by Christoph Busch, a member of the EAB board and professor at the Fraunhofer IGD, who speaks on the “evolution” of research conferences such as this one. His talk is accompanied by graphics showing the course of movement from ape to the human upright walk (fig. 1).

In addition to presented research projects, this year’s conference includes presentations by the Joint Research Center, a so-called EU Science Hub13The main slogan “We are doing science for policy” designates the core tasks of the research center, which was founded in 1957, to provide current EU politics with independent information and evidencing. operated by the European Commission, as well as by representatives of the general directorate of migration and internal affairs of the European Commission (namely Richard Rinkens), the European agency eu-LISA (European agency for the operational management of large-scale IT systems in the area of freedom, security and justice, namely Ciaran Carolan), as well as Frontex (namely Rasa Karbauskaite). The conference’s 2016 track record shows 17 projects and 106 participants.
The boundaries of public research and research according to public interest are blurring into private sector research and development. This is spelled out by the implemented terminology, which the author requires some time to get used to: border guards, travellers or so-called third-country citizens are all referred to as “users”. No matter, whether they appear as clients, research partners or possibly aggrieved parties, wishing not to undergo a border check, they are all operators, or – as stated – users of the presented new systems and technical tools – products that are here advertised as “solutions”. Meanwhile, private corporations are referred to as “organizations”. The contributors, and the respectively presented problems and research projects within the Seventh Framework Programme FP7, or its continuation as a EU work programme for research and innovation Horizon 2020, also contribute to this feeling of vagueness. For example Javier Galbally, who, after his short presentation as a scientist representing JRC and as future chair of the EAB Research Conference,14Javier Galbally, who is a volunteer at the conference in 2016, is supposed to be the chairperson of the EAB conference in 2017. Galbally is engaged as an expert on “reverse biometrics”, “spoofing”, “anti-spoofing” and “biometric vulnerabilities” at the JRC’s department of “E-Space, Security and Migration”, third division for “Cyber & Digital Citizens’ Security”. Currently, the third division is compiling a feasibility report on SIS II, by proxy of the commission, … Continue reading follows up with a second presentation, where he deputies Paolo Salieri of the EU commission and gives an overview over all EU security research projects. One can’t help but get the impression that the community meeting here is doing so for the sake of promoting each other. Galbally identifies border management to be the core focus of security research, applauding EU research programmes for recognizing the outstanding significance of biometrics as a key role. In his impression, Galbally continues, this area is assigned a growing budget each year, especially since the terror attacks in France. Indeed, the Secure Societies work programme of Horizon 2020 fosters a large part of the research presented at the conference.
After the opening, the programme continues with project presentations. Amongst them, Fidelity, a research project (which is now concluded) coordinated by Safran Security and promoted through FP7 where solutions were developed for “people who work on multiple identities”. The project website, concentrating on quality management and standardising breeder documents15A breeder document is a real or forged document, which serves as a basis for other identification documents, which can also be fraudulently attained. and thereby supposedly providing the eponymous confidence, encompasses so-called “white papers” – an umbrella term in the IT sector for standards and technical outline reports. Fidelity, however, generates a “white paper” on privacy, for example, and another on ePassport acceptance. This brings us to a highly important subject, which is also continuously brought up throughout the conference, so-called “privacy by design”. The advantage here lies within the ability to abstain from storing personal biometric data, as the templates can be secured, or transformed into pseudonymous identifiers, e.g. through bloom filter based pseudonymous identifiers, without this process being irrevocable. Another project within FP7 is up next: Fast Pass is continued until March 2017 and incorporates 27 partners. Smooth, fast, automatic, obstacle-free and unopposed, totally trouble-free, that is how this project imagines borders, an image that is projected in great plasticity within the video presentation consistent mostly of simulations. These do show human-human, human-machine and machine-machine interactions, but get by completely without voiceovers. Instead, typical Muzak or elevator music aimed at immobilizing the viewers accompanies them. These sounds are so overly frivolous that I wonder whether the engineers within these projects might not have a certain dystopian relationship to the worlds they are working on. FastPass itself implements a user-focused approach so as to automatize border controls and harmonious architectures, with which they mean border-control-scenarios. The project has expanded the classic setting at the airport (Vienna) to include case studies involving gates (mantraps) or stalls for the Registered Traveller Program (RTP)16The RTP was conceptualized since 2008 and 2013 respectively as part of the so-called Smart Border Package proposed by the commission. After repeated criticism by the European council and parliament with regards to the cost, technological feasibility and implementation, as well as a critical public consultation in 2015, the commission presented a re-worked legislative proposal for smart borders on the 6th of April 2016, which now entailed only the Entry-Exit-System. The realisation of the RTP is … Continue reading at harbours (Piraeus) and country borders (Moravita, Romania). FastPass is working on “next generation sensors”, for “on the move face verification” or a “person separation algorithm”, which is supposed to verify that only one person is located within the gate at a time. Furthermore, FastPass is attempting “document reader interoperability”, developing algorithms to support multimodal biometrics, which is supposed to undermine so-called spoofing – biometric deception. However, it is obvious: FastPass is thought of first and foremost for “Exit Schengen” – or as a conference participant put it:
“I was just wondering, if the project could also be used for Entry Schengen, because you could also hide people in the trunk of your car.”17“Ich habe mich nur gefragt, ob das Projekt auch auf Entry Schengen ausgerichtet ist, weil man ja auch Leute im Kofferraum verstecken könnte.” (transl. S.M.)
MobilePass, a follow-up project to FastPass was conducted in cooperation with the Rumanian and Spanish border patrol for “secure, modular and distributed mobile border control solution for European land border crossing points”. Just as FastPass, it is represented by a spokesperson from the AIT Austrian Institute of Technology. It is the last project before lunch, which takes place at the foyer of the Fraunhofer IGD. Here, we eat standing at whitely shrouded aluminium bar tables, while the surrounding walls stage a comical improvisation of charger cables sticking out of rows of bags and providing invisible gadgets with power. The afternoon continues with the BODEGA project, which is presented by representatives of the VTT Technical Research Centre of Finland, the Greek police, or rather the Center for Security Studies (KEMEA) of the University of Namur, and Thales, each highlighting a different facet of the project. The first contribution conveys a general overview and addresses the “human factor” at borders as central to this type of research.
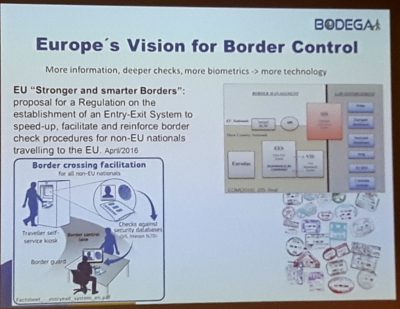
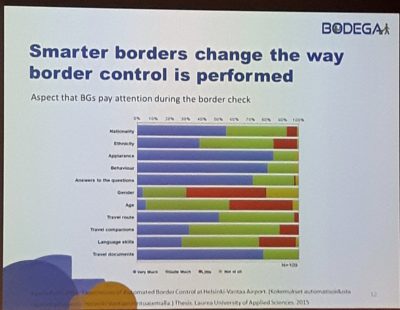
This translates directly into the position of the border guard subject, for whom the project will provide a “toolbox”. The summary of the project description is formulated in more figurative language, as the “ethical societal dimension” and “proactive enhancement of human performance in border control” is discussed. In contrast to pilot and feasibility studies, BODEGA attaches utmost importance to the field and relies on field research to generate data – just as is usually the case within ethnographically inspired qualitative social research. “Smarter borders change the way border control is performed”, says the presenter, Blagovesta Nikolova. She is implying that an increasingly automated border will change the attention economy of border guards, thereby altering the interaction between the “end users”, travellers and border police (fig. 2, fig. 3).
The project, I begin to realize, aims at improving the performance of border guards in the time after the implementation of programmes, such as the RTP and other variants of an intelligent border through increasing mechanisation, computerisation and automation. If nothing else, the point is to flank EU policy initiatives such as the Smart Border package with research already going well beyond it. Nikolova, who is employed by the Laboratory for Ethical Governance of Information technology at the university of Namur and has taken two projects to the conference in Darmstadt, highlights the ethical dimensions of border management contexts in her presentation. Her emphasis is that the proposed work package does not simply evolve around technology acceptance and questions of ethical research, but includes an attempt to establish “research reflexivity” framed by Responsible Research and Innovation (RRI), and annexed with transversality. As this sounds promising, I approach her in the break to ask about publications regarding the matter, as I could find none online, even after months into the project term. Unfortunately, these “deliveries” are solely internal and not available to the public, “due to safety reasons”, says Nikolova. The analysed “deep implications” of the technologisation discussed here, which are meant to advance security and velocity at borders are again a safety risk? An interesting aspect of this could be the noted functional transition of the border from a dividing line, or scene of separation, to a place of information retrieval. Fourth and last up to speak about the BODEGA research project is the psychologist Elise Le Guellec from Thales. She complements the demonstration of BODEGA as multi-disciplinary. Self-proclaimed “human factors expert”, she presents first results of the field research. The main aspect in the field, she underlines, was to accompany the border guards for an entire shift. It is notable that these ethical, social or psychological “zooms on soft skills” are mostly conveyed by women, while the technological aspects are all portrayed by men: “Humans are part of your system, so do not forget about them when you design a system”, Le Guellec recites.
The following presentations cover the project Origins, which concentrates on verifying and standardising birth certificates as the traditional document most prone to forgery,18One of the slides on the projected power point presentation states, 2009 saw almost 13900 cases of document fraud in France. 6.300 of those were uncovered by the border police, in 4011 of these cases, French documents were affected: 1.640 birth certificates, 1.070 identity cards, 1.035 passports and 266 drivers’ licenses. Ekzistenz, which develops strategies against identity theft and wants to guarantee one safe identity for every EU citizen,19One example, with which the speaker illustrated the virulence of the project, was also telling the case of a French woman, married to an Algerian on paper, who claimed that the document was fraudulent. This confronted her with an extremely complicated burden of proof. and HECTOS, a project going beyond biometrics and focusing on physical attacks as well as certifying and harmonising evaluation processes. Numerous projects represented at the conference focus on the biometrically anchored enforcement of a unique identity within a single breeder. These projects are compliant to building European standards. In direct contrast are of course migrant tactics and quotidian practices Helle Stenum describes in her article as “strategies of flexible identities”20“Strategien einer flexiblen Identität” (trans. S.M.).: obtaining papers and handing off registrations make up equal parts and are met with a response that Dennis Broeder accurately formulates as a modulation between “exclusion from registration and documentation” and “exclusion through registration and documentation”21Dennis Broeders, “A European ‘Border’ Surveillance System under Construction”, in: Huub Dijstelbloem and Albert Meijer (eds.), Migration and the New Technological Borders of Europe, Basingstoke, Palgrave Macmillan, 2011, pp. 40–67. It shall be explicitly stated here, that the modulation of exclusion described by Broeder, does not end with citizenship, as most cases of “reversible citizenship” in Europe show, cf. hic: Vassilis Tsianos and Marianne Pieper, “Postliberale … Continue reading.
The day ends with Joseph Cannataci, a well-known data specialist, moderating a panel titled “How will biometric systems change – with the new EU regulation on Data Privacy”. The focus lies on the EU’s most recent data security policies, the General Data Protection Regulation (GDPR), which advocates “privacy by design and by default”. Evgeni Moyakine, Claudia Colonnello and Catherine Jasserand-Breeman are on the panel talking about the rights of data subjects, such as the “right of consent to the data collection” and the “right of erasure of data” by example of the Speaker Identification Integrated Project (SIIP). The question is, how these rights can be implemented into the respective systems. I begin to grasp an important point of “privacy by design”, which is the possibility of bridging the gap between various disciplines. Interdisciplinary knowledge and knowledge mediation are all rage. On top of that, “privacy by default”, the standardized data-security-friendly setting of products and services, opens up questions of the social, as products and services are developed and constructed in the age of “big data” and “open data”. Data security was thought as “impact assessment” to date, claims Claudia Colonnello of the Italian Laboratoria di Scienze della Cittadinanza (LSC). The new paradigms of rights and liberties of natural people as put forth through article 25 of the new EU data security regulations (EU-DSGVO) “data security through technical design and privacy friendly default settings”22“Datenschutz durch Technikgestaltung und durch datenschutzfreundliche Voreinstellungen” (trans. S.M.). and others, clarify that a form of “societal impact assessment” is necessary today. Joseph Cannataci’s arguments go in a similar direction, as he describes a cultural change in thinking about what “privacy” means today.
The conference continues on the subject of identity management infrastructure in Europe (Future ID), identity theft (SWAN, Secure Access Control Over Wide Area Network), enhanced fingerprint live-scan technology (INGRESS) and a platform for standard operational evaluations for biometric technologies (BEAT). Subsequently, a representative of Indra Sistemas presents ABC4EU, research that engages with sorting processes at borders. Purpose of the project is to develop Automated Border Control Gates for Europe, so that “manual intervention” or “operator involvement” is necessary only on rare occasions. This project, too, clearly anticipates the implementation of the Registered Traveller Program (RTP) and the Entry-Exit-Systems (EES). The prototypes and pilot projects are presented in expectance of an implementation of the most recent smart border regulation plans from April 2016.23Cp. European Commission, “establishing an Entry/Exit System (EES) to register entry and exit data and refusal of entry data of third country nationals crossing the external borders of the Member States of the European Union and determining the conditions for access to the EES for law enforcement purposes and amending Regulation (EC) No 767/2008 and Regulation (EU) No 1077/2011”, Proposal for a Regulation of the European Parliament and of the Council, COM(2016) 194 final, April 6, 2016. … Continue reading Nonetheless, the actual test series needs to be conducted in “real scenarios” and also respond to the then valid legal situation. The Spanish company Eticas Research & Consulting works most centrally at gaining acceptance from the general public for the integration of the projects. This concerns the approval of integrating whole-body scanners at airports, for example. A crucial point would be expanding privacy protection “from legal to desirable and acceptable to privacy-enhancing”, says presenter Gemma Galdón Clavell, accompanying her talk with a graphic display of the methodology that Eticas Research & Consulting has been implementing successfully for five years (fig. 4).
According to her, an application-oriented understanding and implementation of the ABC Gates would be fundamental. Therein, she is yet another speaker underlining the changed role of border guards, whose function is gradually altered to “helping one to pass through a system” – in her example, someone with mobility restrictions. The next speaker, Cristina Conde of the University Rey Juan Carlos, counts as a distinguished expert in the field of face recognition biometrics. I, too, am fascinated by the way in which she narrates the attack on a biometric system – facial recognition. She reports on the interaction of artefacts as if it was natural. While there may somewhere be a “hurtful purpose”, this seems rather irrelevant for “biometric vulnerability”, the vulnerability of the system through spoofing. While the scientist assesses the technological quality of the artefact, with which an attack is made, to be very high, she deems the reason, motivation or intention of surpassing biometric control barriers to be barely notable. Her focus is on the self-defence mechanisms of the system. Therefore, the plot concentrates on sensors (hardware), characteristics (software), or fusion strategies (score-level). The next speaker of the Università degli Studi di Milano engages with multi-biometric systems and “information fusion”, where the “match score level fusion” technique offers the best results, or at least better than the fusion of sensors and characteristics. Vision Box, ABC4EU’s industrial partner, offers the last speaker of the segment. The Vision Box website speaks of “happy flow”, and of an “ultimate passenger experience”, which is becoming “easier, faster and safer”. “eMRTD’s” are mentioned ceaselessly, a shorthand for “Electronic machine-readable travel documents”. I notice first signs of fatigue, and my eyes and thoughts begin to wander. Panayiotis Mertis of the Hellenic police/KEMEA is seated a couple of rows before me and on his computer screen I can see him gazing at the same pictures as me, the burning refugee camp Moria on the island of Lesbos. The news of the fire and subsequent flight of over 3000 inhabitants had been flying in from there since late evening of the lecture. The so-called hotspot holds the data of all arrivals from the border until establishing identification for registration. As conditions are miserable and delays immense, migrants are demanding to be allowed to travel to Athens.24On the fire, cp. e.g.: Die Welt, “Tausende Flüchtlinge irren nach Brand auf Insel umher”, September 20, 2016. Available at: https://www.welt.de/politik/ausland/article158262874/Tausende-Fluechtlinge-irren-nach-Brand-auf-Insel-umher.html [accessed September 20, 2016]. On the hotspot Moria cp e.g.: Brigitta Kuster and Vassilis S. Tsianos, Hotspot Lesbos. Eine Publikation der Heinrich-Böll-Stiftung, Heinrich Böll Stiftung, August 2016. Available at: … Continue reading
Subsequent to this, representatives of Veridos identity solutions GmbH/Bundersdruckerei, Intrepid minds and the Laboratory for Ethical Governance of Information Technology of the University of Namur present PROTECT. The project, fully titled “Pervasive and UseR Focused BiomeTrics BordEr ProjeCT”, kicked off recently and has a run-time of three years. It’s all about “breaking the limits” and “really innovative scenarios”, and about “remote biometrics”. Instead of border gates or stalls, where border control is more or less automated, PROTECT proposes passages and corridors, through which travellers must pass. Based on the observation that this border scenario is not compatible with the Schengen code, where data-storage of EU citizens is not allowed, someone from the audience asks, whether PROTECT is intended only for third-country citizens. The response proclaims that the project first and foremost proposes a technological vision. Indeed, the vision goes far beyond the Entry-Exit-System already in place (fig. 5, fig. 6, fig. 7).
However, such futurism is exactly what is needed to reengage exhausted listeners such as myself. Intrepid Minds, a company specialized on producing events in the area of financial markets, rights and governance, has its speaker emphasise the research character of PROTECT will go beyond the visionary, to learn from past failures. The call for projects reads “explore”, not “answer”. And:
“my vision is that someone activates the function on their mobile, crosses the corridor, and then disables the function again”25“Meine Vision ist, dass jemand die Funktion aktiviert auf seinem Handy, durchgeht durch den Korridor, und die Funktion dann wieder ausschaltet.” (transl. S.M.).
Quietly, and in a deliberately casual manner he adds, he hopes not only that travellers consent to the corridors, but that they will also prefer them. The aim is not just acceptance, but a free decision. And even the usual procedure of questions regarding the project is turned on its head, as the speaker rhetorically states the questions he wants to research through PROTECT:
“Can we? May we? Should we?”
Within the realm of “legal, ethical and social issues”, “privacy enhancing” on the one, and the mantra-like emphasis on “trust building” on the other side are routinely presented throughout the PROTECT presentations. The innovation, says the speaker from Namur, lies within producing suggestions, not commands for engineers. The engineers should themselves be motivated to develop ethical questions, and work them into the systems. PROTECT, too, aims at creating interdisciplinary collaborations between social sciences, engineers and juristic specialists. Nonetheless, it seems to me, as if jurisprudence and the humanities are engaged to moderate meaning, rather than critically accompanying the development of new practices.
All projects share a motivation, a self-legitimization even, through a constantly growing number of travellers within the EU: An estimate of the European Commission is referenced again and again, which states that 2025 will bring 302 million border passages into Europe, and 76 million third-country nationals (TCN). Calculating with numbers from 2014 that would mean an increase of 55%. It is therefore logically consistent that all research projects have a common focus on “pervasive, minimally-intrusive, rapid and usable identity confirmation systems”. A delay in mobility fluxes at borders should be prevented at all costs – as the set phrase astoundingly reveals:
“Crowding should be avoided ‘for many reasons’.”
Finally, an own contribution on the Entry-Exit System, or rather, on the existing and scheduled “EU Large Scale Systems” within the EU agency by eu-LISA marks the conclusion. Speakers from the European commission, the private sector, academics, Frontex and eu-LISA itself present within this panel. Ciaran Carolan gives a first, quite technical keynote. He presents the biggest “operational biometric testing” ever conducted in Europe to date, the Smart Border pilot study (fig. 8).
Carolan seems happy to share the relevant results of the study, as:
“this is why meetings such as this one are so important. So that we can tell you, what research is needed”26“Deshalb sind Treffen wie dieses so wichtig, damit wir euch sagen, welche Forschung gebraucht wird.” (transl. S.M.)
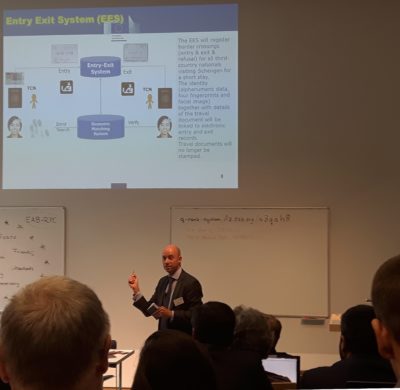
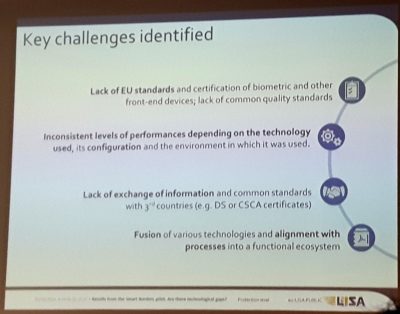
Richard Rinkens, project manager for biometrics at DG Home Affairs, picks up on this line of impact in his contribution titled “Requirements for research derived from the Smart Border Concepts”. So does the final panel “Mind the gap – what research is needed for current and future operational biometric systems”27The subject of cryptotechnology and the area of behavioural biometrics were also mentioned here, although Rasa Karbauskaite of Frontex spoke of “nervous behaviour” at the border and stated that Rumania had conducted “respective test series”. Jean-Christophe Fondeur of Safran Identity & Security stated in following that behavioural biometrics were an “immature technology”.. The bouquet of results and assessments of technological gaps within the EES presented here translate into a direct work assignment for the EAB Research Projects Conference’s audience. The EES clearly aims at surveying the group of overstayers. This is by no means disguised, but directly addressed. As things are now, the survey made easily possible through EES, would theoretically be calculated from each stamped passport in an arduous process without it – an almost unfeasible task according to Rinkens, whose presentation style is lively, popular and humorous (fig. 9).
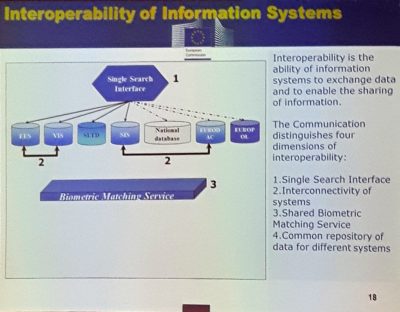
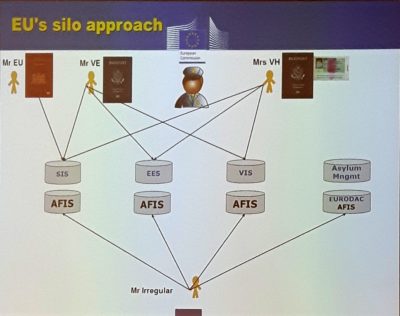
His contribution also addresses the buzzword “interconnectivity”. In connection to eu-LISA, interconnectivity calls privacy advocates and human rights actors into action, but also ill-informed politicians, susceptible to conspiracy theories, says Rinkens. However, it is necessary to strictly distinguish interconnectivity from interoperability. The difference between the two is illustrated through a diagram. According to the current situation, which he terms the “EU’s silo approach”, there are one planned and three large existing EU datasystems: EES, VIS, SIS, and the oldest, Eurodac (fig. 10).
These systems are merely partially connected, even though a single matching platform secures their interoperability (fig. 11).
The conclusion Rinkens draws from this is a EU-wide “identity repository” as a long-term goal.
“A common repository of data at EU level for different systems is the most ambitious long-term approach to interoperability. This core module would contain basic identity data while specific data (e.g. visa data, entry/exit records, ETIAS records) would be stored in specific modules. This would overcome the current fragmentation of the EU’s data architecture.”
The DG Home Affairs, just as the police force, seem strained by all the different databases. The following discussion evolving around “large databases” vs. “centralized databases” suggests that from a technological point of view it is highly debatable, whether centralised or decentralised databases and possibly federated identity-management-systems are more vulnerable and prone to attacks. However, consensus within the conference does exist on the technological and governmental aspects, which should most likely go hand in hand, while “policy makers” are known to go against that grain. All participants of the EAB Research Project Conference hope that the developments of large European biometric data systems follow a technological decision process, instead of a political one.
Before departure, the final panel is opened to the public for questions. At the beginning of the session, Christoph Busch had already drawn up a whiteboard, where he shows what the EU and the EAB represent in equal measure. The terms “innovation”, “peace”, “friends”, “standards”, “diversity” and “democracy” are arranged in a star-shaped formation. However, as far as “democracy” in connection with the EAB is rather questionable, he proposes a system, within which all conference participants can equally upload questions to a server anonymously. It is also possible to rate the already registered and uploaded questions posed by others. Hence, the end of the conference is made up by a prioritized list of questions. This installed q-rate system is evidence of a cybernetic adjustment to the diagnosed deficit of democracy (fig. 12, fig 13).
Translated by Sara Morais.
| ↑1 | Cp. Brigitta Kuster and Vassilis Tsianos, “How to Liquefy a Body on the Move: Eurodac and the Making of the European Digital Border”, in: Raphael Bossong and Helena Carrapico (eds.), EU Borders and Shifting Internal Security. Technology, Externalization and Accountability, Heidelberg, Springer International Publishing, 2016, pp. 45–63. |
|---|---|
| ↑2 | “Ein Beitrag zur Erhöhung der inneren Sicherheit in Europa” (transl. S.M.). |
| ↑3 | “Dieses Jahr müssen wir zu einer politischen Einigung über die Eckpunkte eines Ein- und Ausreiseregisters (Entry-Exit-System, EES) kommen und wir sollten eine Einbeziehung von EU-Bürgern prüfen. Wir brauchen zudem noch in diesem Jahr eine Einigung über die Einrichtung eines Europäischen Reiseinformations- und Genehmigungssystems (ETIAS).” (transl. S.M.) |
| ↑4 | Cp. David Lyon, “Identification, colonialism, and control: surveillant sorting in Israel/Palestine”, in: Elia Zureik, David Lyon and Yasmeen Abu-Laban (eds.), Surveillance and Control in Israel/Palestine. Population, Territory and Power, London/New York, Routledge, 2011, pp. 49–64. |
| ↑5 | Examples for this include the Sistema Integrado de Vigilancia Exterior, the integrated electronic system for outdoor surveillance SIVE in Spain, or the EU-wide border surveillance system called EUROSUR. |
| ↑6 | Ben Hayes, NeoConOpticon –The EU Security-Industrial Complex, Transnational Institute in association with Statewatch, 2009. Available at: http://www.statewatch.org/analyses/neoconopticon-report.pdf [accessed May 30, 2017]. |
| ↑7 | Bastiaan van Apeldoorn and Laura Horn, “The Marketisation of European Corporate Control: A Critical Political Economy Perspective”, New Political Economy, 12(2), 2007, pp. 211–235. According to these authors, the process of European integration, which has been driven by a project of neoliberal marketization since the late 1980s, has played a leading role in the emergence of European shareholder capitalism. Entering new markets is important in terms of the competition European industries face through the USA and China. On a global scale, the security industry is expanding powerfully, and has seen a growth of almost tenfold in the last ten years. 2011 it amounted to a market size of 100 billion. |
| ↑8 | The authors of a paper published by the German Institute for International and Security Affairs, SWP titled “Border Security, Camps, Quotas: The Future of European Refugee Policy?” highlight that Frontex has ten times as many employees as when the agency was founded, while their annual budget has risen from six to 245 million Euros. Cp. Steffen Angenendt, David Kipp and Anne Koch, “Border Security, Camps, Quotas: The Future of European Refugee Policy?”, SWP Comments 2016/C 32, June 2016. Available at: https://www.swp-berlin.org/en/publication/border-security-camps-quotas-the-future-of-european-refugee-policy/ [accessed June 24, 2017]. |
| ↑9 | Frontex for example made headlines on the 27th and 28th of January 2016 through a pitch on Lesbos. Securiport LLC, Crossmatch, Unisys, Thales and 3M were invited to present suggestions for a design of smartphone apps and databases to track refugees arriving in Europe. For a more detailed discussion see: Diane Taylor and Emma Graham-Harrison, “EU asks tech firms to pitch refugee-tracking systems”, in The Guardian, February 18, 2016. Available at: https://www.theguardian.com/world/2016/feb/18/eu-asks-tech-firms-to-pitch-refugee-tracking-systems [accessed June 24, 2017]. |
| ↑10 | Cp. Kaushik Sunder Rajan, Biokapitalismus. Werte im postgenomischen Zeitalter, Frankfurt a. M., Suhrkamp, 2009, p. 122. |
| ↑11 | Central to this, especially when considered as switch points or points of intersections of the EU-network between the private sector and the EU-administration, as well as the legislative, are above all the EU research framework programmes, such as Horizon 2020, which concern the “research and innovation” programmes. For example, the Seventh Framework Programme FP7, initiated in 2007, focuses heavily on security. The commission has provided the programme with 1,4 billion Euros with a run-time until 2013. The follow-up project Horizon 2020 categorizes the subject of border management under “societal challenges” and collectively frames these under the heading “secure societies – Protecting freedom and security of Europe and its citizens”. Horizon 2020 has received a budget of around 80 billion Euros for a run-time of seven years (2014-2020). This comes in addition to any private investments it can draw on. Cp. Chris Jones, “Analysis. The visible hand: the European Union’s Security Industrial Policy”, Statewatch, August 2016. Available at: http://www.statewatch.org/analyses/no-297-security-industrial-policy.pdf [accessed June 24, 2017]. |
| ↑12 | The Fraunhofer IGD (Institute for graphic data processing) broadly speaking engages with the problems and possibilities in operating with computer data within hard- and software. Founded in 1992, it upholds a total of twelve research and development divisions located in Darmstadt, Rostock, Graz and Singapur, which work closely with the respective technical universities, as well as with clients and partners from industrial and economic sectors. The Fraunhofer IGD is internationally recognized as a leader in applied research of visual computing and is a part of the “Fraunhofer Gesellschaft”, the biggest research organisation for application-oriented research in Europe. |
| ↑13 | The main slogan “We are doing science for policy” designates the core tasks of the research center, which was founded in 1957, to provide current EU politics with independent information and evidencing. |
| ↑14 | Javier Galbally, who is a volunteer at the conference in 2016, is supposed to be the chairperson of the EAB conference in 2017. Galbally is engaged as an expert on “reverse biometrics”, “spoofing”, “anti-spoofing” and “biometric vulnerabilities” at the JRC’s department of “E-Space, Security and Migration”, third division for “Cyber & Digital Citizens’ Security”. Currently, the third division is compiling a feasibility report on SIS II, by proxy of the commission, for instance. The division also has an advisory function to the DG Justice with regards to the fingerprint-identification system of the European Criminal Records Information System (ECRIS). Galbally himself is currently working on the integration of AFIS for SIS II and on a mobile app for third-country nationals to download, so they can be registered within the Entry-Exit-System in advance. |
| ↑15 | A breeder document is a real or forged document, which serves as a basis for other identification documents, which can also be fraudulently attained. |
| ↑16 | The RTP was conceptualized since 2008 and 2013 respectively as part of the so-called Smart Border Package proposed by the commission. After repeated criticism by the European council and parliament with regards to the cost, technological feasibility and implementation, as well as a critical public consultation in 2015, the commission presented a re-worked legislative proposal for smart borders on the 6th of April 2016, which now entailed only the Entry-Exit-System. The realisation of the RTP is therefore left to the single member states. |
| ↑17 | “Ich habe mich nur gefragt, ob das Projekt auch auf Entry Schengen ausgerichtet ist, weil man ja auch Leute im Kofferraum verstecken könnte.” (transl. S.M.) |
| ↑18 | One of the slides on the projected power point presentation states, 2009 saw almost 13900 cases of document fraud in France. 6.300 of those were uncovered by the border police, in 4011 of these cases, French documents were affected: 1.640 birth certificates, 1.070 identity cards, 1.035 passports and 266 drivers’ licenses. |
| ↑19 | One example, with which the speaker illustrated the virulence of the project, was also telling the case of a French woman, married to an Algerian on paper, who claimed that the document was fraudulent. This confronted her with an extremely complicated burden of proof. |
| ↑20 | “Strategien einer flexiblen Identität” (trans. S.M.). |
| ↑21 | Dennis Broeders, “A European ‘Border’ Surveillance System under Construction”, in: Huub Dijstelbloem and Albert Meijer (eds.), Migration and the New Technological Borders of Europe, Basingstoke, Palgrave Macmillan, 2011, pp. 40–67. It shall be explicitly stated here, that the modulation of exclusion described by Broeder, does not end with citizenship, as most cases of “reversible citizenship” in Europe show, cf. hic: Vassilis Tsianos and Marianne Pieper, “Postliberale Assemblagen: Rassismus in Zeiten der Gleichheit”, in Sebastian Friedrich (ed.), Rassismus in der Leistungsgesellschaft, Münster, Ed. Assemblage, 2011, pp. 114–132. |
| ↑22 | “Datenschutz durch Technikgestaltung und durch datenschutzfreundliche Voreinstellungen” (trans. S.M.). |
| ↑23 | Cp. European Commission, “establishing an Entry/Exit System (EES) to register entry and exit data and refusal of entry data of third country nationals crossing the external borders of the Member States of the European Union and determining the conditions for access to the EES for law enforcement purposes and amending Regulation (EC) No 767/2008 and Regulation (EU) No 1077/2011”, Proposal for a Regulation of the European Parliament and of the Council, COM(2016) 194 final, April 6, 2016. Available at: https://ec.europa.eu/home-affairs/sites/homeaffairs/files/what-we‑do/policies/securing‑eu‑borders/legal‑documents/docs/20160406/regulation_proposal_entryexit_system_borders_package_en.pdf [accessed April 6, 2016]. |
| ↑24 | On the fire, cp. e.g.: Die Welt, “Tausende Flüchtlinge irren nach Brand auf Insel umher”, September 20, 2016. Available at: https://www.welt.de/politik/ausland/article158262874/Tausende-Fluechtlinge-irren-nach-Brand-auf-Insel-umher.html [accessed September 20, 2016]. On the hotspot Moria cp e.g.: Brigitta Kuster and Vassilis S. Tsianos, Hotspot Lesbos. Eine Publikation der Heinrich-Böll-Stiftung, Heinrich Böll Stiftung, August 2016. Available at: https://www.boell.de/sites/default/files/160802_e‑paper_kuster_tsianos_hotspotlesbos_v103.pdf [accessed June 24, 2017]. |
| ↑25 | “Meine Vision ist, dass jemand die Funktion aktiviert auf seinem Handy, durchgeht durch den Korridor, und die Funktion dann wieder ausschaltet.” (transl. S.M.) |
| ↑26 | “Deshalb sind Treffen wie dieses so wichtig, damit wir euch sagen, welche Forschung gebraucht wird.” (transl. S.M.) |
| ↑27 | The subject of cryptotechnology and the area of behavioural biometrics were also mentioned here, although Rasa Karbauskaite of Frontex spoke of “nervous behaviour” at the border and stated that Rumania had conducted “respective test series”. Jean-Christophe Fondeur of Safran Identity & Security stated in following that behavioural biometrics were an “immature technology”. |
Brigitta Kuster is an artist and cultural researcher, primarily interested in visual and film studies, postcolonial relations, and migration and border studies.