Galton’s Utopia – Data Accumulation in Biometric Capitalism
“To divide, deploy, schematize, tabulate, index, record everything in sight (and out of sight); to make out of every observable detail a generalization and out of every generalization an immutable law about the Oriental culture […] are the features of Orientalist projection.”1Edward Said, Orientalism, New York, Vintage Books, 1979, p. 86.
Edward Said
“The mathematical efficiency of the biometric state brings with it possibilities for storing and processing data, and for generating feedback about the behaviour of individuals that was simply unmanageable in a paper bureaucracy. This brings us much closer to the all-knowing cybernetic state that Norbert Wiener predicted long ago, and it gives a chilling edge to Habermas’ worries about the steering effects of the ‘technicizing of the lifeworld’. How this all works in practice remains to be seen, but it is, I think, fair to say that both Wiener and Habermas would be surprised that this technologically precocious state is taking form outside of the developed West.”2Keith Breckenridge, Biometric State: The Global Politics of Identification and Surveillance in South Africa. 1850 to the Present, Cambridge, Cambridge University Press, 2014, p. 9.
Keith Breckenridge
Introduction
The US-led invasion of Iraq in 2003 and its goal to achieve biometric identity dominance through activities that link “an enemy combatant or similar national-security threat to […] previously used identities and past activities”, turned the city of Fallujah into “Camp Fallujah”: a testing ground for biometric applications.3John D. Woodward, Jr., “Using biometrics to achieve identity dominance in the Global War on Terrorism”, Military Review, September/October 2005, pp. 30–34.
In 2007, Journalist Noah Shachtmann described this situation in his Iraq Diary: Fallujahs’s Biometric Gates:
“The Marines have walled off Fallujah, and closed the city’s roads to traffic. The only way in is to have a badge. And the only way to get a badge is to have Marines snap your picture, scan your irises, and take all ten of your fingerprints. Only then can you get into the city. […] Putting the system in place can be… well, tedious doesn’t even begin to describe it. One Iraqi after another walks into this converted schoolhouse, ringed with sandbags and razor wire. One Iraqi after another is asked their name, their tribe, and told to put their fingers on the glowing green scanner.”4Noah Shachtmann, “Iraq Diary: Fallujah’s Biometric Gates”, Wired, August 31, 2007. Available at: https://www.wired.com/2007/08/fallujah-pics/ [accessed September 2018].
This essay looks at the evolution of biometric techniques for identification and control by connecting the historical emergence of biometric fingerprinting in the Colonial and Industrial Age with today’s “war on terror” by using Fallujah as a recent case. Biometrics claims that the key to a person’s identity is not her incommensurable, unique, and individual character traits, but rather the tactile presence of her body in the world, as Allan Sekula writes.5Cp. Allan Sekula, “The Body and the Archive”, October, 39, 1986, pp. 3-64. The twisted and standardized ways that biometrics recognize bodily presences, is the topic of this text. Biometrics purports to ask: Are you who you say you are? Yet, for Iraqis suspected to be connected to terrorist networks, this sounds more like: You are whatever I say you are.
In reading together the recent case of Fallujah and the historic socioeconomic conditions of the birth of modern fingerprinting in the Victorian Age, this text shows how biometrics were created through the construction of suspicious and risky subjects. In doing so, it dismantles the narrative of neutral technology that just “reads” from the “natural” body as it “is”. Additionally, it proposes that the construction of a suspect population today is entangled with the formation of a surplus population: Iraqi citizens were used to test and improve biometrics and extract data. This situation is part of a hidden history of experimentation, dispossession, and accumulation that will be addressed in this text.6I borrow the term “hidden history of experimentation” from Katja Lindskov Jacobsen, “Making Design Safe for Citizens: A Hidden History of Humanitarian Experimentation”, Citizenship Studies, 14 (1), 2010, pp. 89-103.
While ideas of white supremacy and the violent invention of race as a category organised western belief systems, beauty standards, and colonial capital, this text looks at how marginalized bodies were used as “material capital” to build the biometric apparatus. This essay examines how fingerprints, facial features and irises were accumulated, classified, and rearranged into new identities, mirroring the division of labour so central for the rise of the Industrial Age. It examines how individuals were, from the perspective of the western eyes, objectified into suspicious subjects, dehumanised, and stripped of agency, history, and intelligence in order to become biometric data points in the emerging grids of state, military, and corporate intelligence, although resistance to these procedures was widespread throughout history. In asking who the producers of biometric apparatuses are, it provokes to take into account the accumulated social labour and collective intelligence that was involved in the process.7Social labour and collective intelligence are used to emphasize an approach that understands biometrics as a socio-material assemblage and looks at its collective and social dimension in the sphere of production. This essay will foreground the fact that Iraqi citizens as collective producers were needed to animate and improve the biometric apparatus; with Fallujah as the site for data extraction. See also Matteo Pasquinelli, “Italian Operaismo and the Information Machine”, Theory, Culture … Continue reading
Galton’s Desire for “True” Biometric and Racial Knowledge
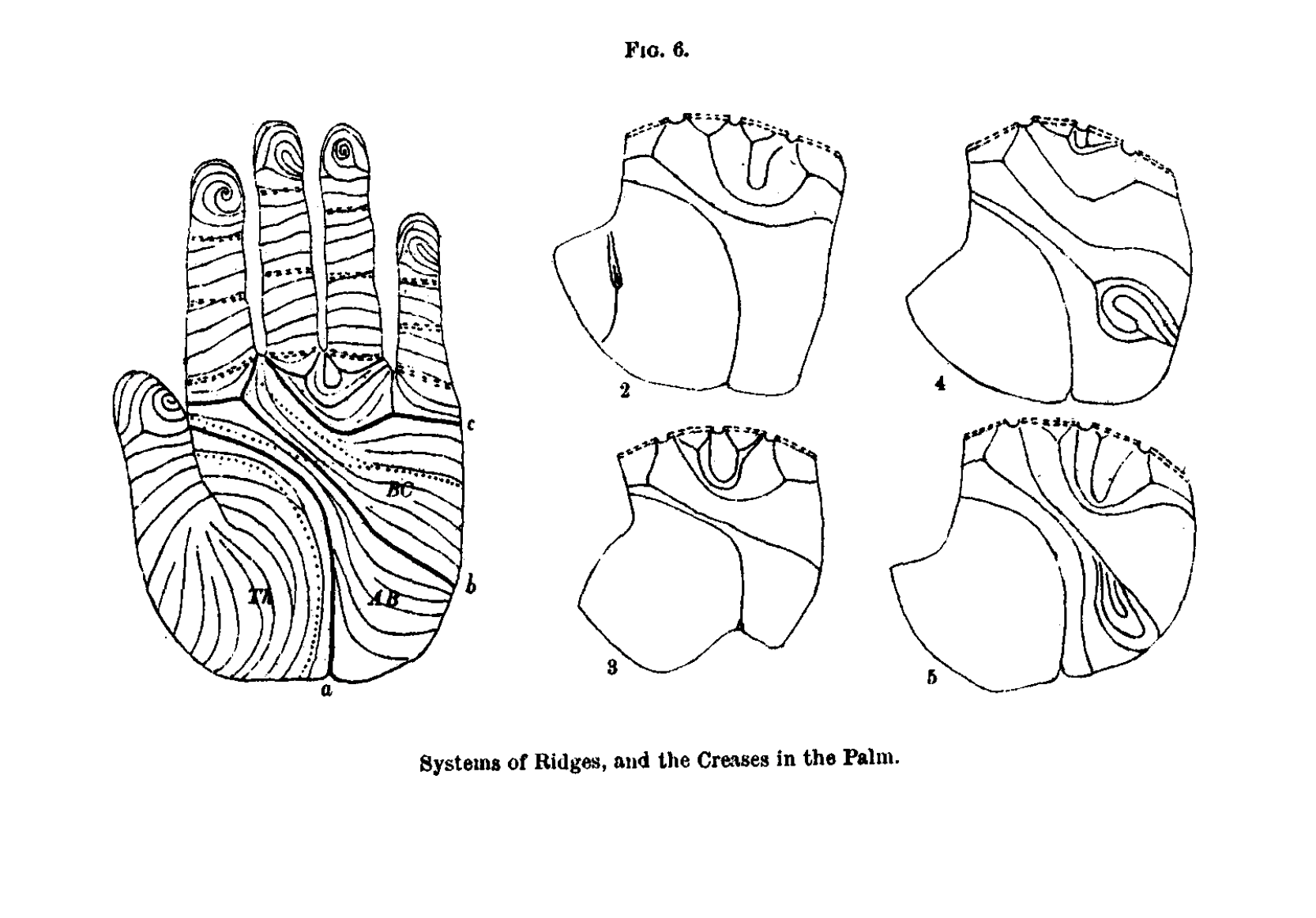
The birth of modern biometrics can be situated within the socioeconomic climate of the Industrial Revolution in late 19th century England. Within this history, the statistician and eugenicist Francis Galton serves as an important figure. Galton was fascinated by the power to capture physiological characteristics, which, to him, promised a new era of exactitude and intelligibility. This era would leave the fallible world of writing behind, using the uniqueness of the human body as a new medium. “The ridges [of the fingerprints] are in some respects the most important of all anthropological data,” he wrote. Origins, islands, and enclosures in each fingertip form a unique pattern of arches, whorls, and loops that are nearly permanent.8Cp. Francis Galton, Finger Prints, London/New York, Macmillan & Co, 1982, p. 2.
During the formation of the early modern nation states in Europe, biometric identification techniques emerged as a way to formalise and organise subjects into graphs and tables. Fingerprinting, as Galton’s emphatic statement underlines, set out to become the dominant form of identification during the second half of the 20th century.
In his book Biometric State: The Global Politics of Identification and Surveillance in South Africa, Keith Breckenridge describes how emerging modern forms of governance differed from older forms of power. “Biometric states” that implemented fingerprinting were much more efficient in storing and processing data. As biometric systems improved over time, they allowed governments to identify and generate feedback about the behaviours of individuals.
According to Breckenridge, fingerprinting also worked on an epistemological level as it shifted the meaning of the word “evidence” itself. The process of gaining evidence had for centuries implied oral testimony and access to the world through human vision and cognition. In the age of biometrics, however, evidence is intimately linked to the power of numbers, calculation, and highly “abstracted forms of statistical knowledge”9Keith Breckenridge, Biometric State, p. 29..
The statistical abstractions of this new biometric regime are part of Francis Galton’s world; a world that paved the way for technopolitical forms of governance. In examining the genesis of fingerprinting, one is able to see how the new regime of governing through calculation was shaped and how it became part of a computational intelligence that can now no longer be accessed through human vision and cognition. Instead, it needs a machinery, an algorithm.
Galton worked on his fingerprinting classification system in Victorian South Kensington in the 1880s. The system he devised in his laboratory laid the foundation for automated industrial-style identification, which has since spread throughout the world. Galton’s system is an early form of pattern recognition. Fingerprints were captured, indexed, and classified manually – a laborious task in contrast to today’s sophisticated forms of automated pattern recognition. What both forms have in common is that, at their technological core, they make use of mathematical functions and statistics to find meaningful patterns. In doing so, they establish a rigid system of classification in data that is otherwise illegible to a human operator.
An important aspect of Galton’s biometric regime is the fact that fingerprinting was first tested and shaped outside the West. By examining fingerprints in the colonies, Galton intended to find evidence that race existed as a hidden order. He claimed that the distinct features of “natives” could only be perceived with great difficulty to the western eye, implying that all indigenous people looked the same. This argument served to legitimate his project.10Cp. Francis Galton Finger Prints. Inspired by previous fingerprinting research in colonial India, Galton’s quest took him through the modern disciplinary institutions of the army, hospitals, schools, asylums, and prisons where he incessantly analysed the statistical output of arches, ridges, and whorls; the minutiae of fingerprints captured on glass plates or paper.
Biometric Capital in the Identification Economy
The author and filmmaker Hito Steyerl recently stated that “identity is the name of the battlefield over your code – be it genetic, informational, pictorial.”11Hito Steyerl in Conversation with Marvin Jordan, “Hito Steyerl. Politics of Post-Representation”, Dismagazine. Discover, n.d. Available at: http://dismagazine.com/disillusioned-2/62143/hito-steyerl-politics-of-post-representation [accessed August 27, 2018]. The battle for sovereignty over identity-codes is, however, distributed unevenly. It varies in terms of geography and intensity, depending on who is denoted by Steyerl’s “you”.
The 2003 Iraq War, the US used biometrics in their battle to achieve their biometric identity hegemony. The battlefields and ruins of Fallujah served as the background for the biometric mass registration of Iraqi citizens under siege. In Fallujah, the relationship between productive and destructive forces becomes apparent. Reflecting on this relationship, the film essayist Harun Farocki remarked that “economics demand wars with maximum precision targeting. Such as: wars fought on humanitarian grounds”.12Harun Farocki, A Way, 2005, https://www.harunfarocki.de/installations/2000s/2005/a-way.html, accessed August 31, 2018. Biometric control and surveillance enables operations of high precision at micro and macro scales in that it is able to target individuals, groups, and populations. How are these humanitarian grounds – intrinsically linked to sites of conflict and war – connected to economics?
To answer this question, we might begin with the observation that lucrative technologies, for instance biometric ID cards, are often tested in so-called developing and unstable regions. Refugee camps, areas of crisis, and war-torn regions have little to no privacy regulations. These are sites of trial and error, with weak boundaries between the state and private corporations. Within such regions, states are often unable to register their populations. Private corporations offer quick and cheap infrastructure in return for data and access to the biometric banking industry.13In Nigeria, for instance, Mastercard has issued national biometric ID cards that people can also use to pay and vote.
Biometrics are a colonial practice, but they also emerged within what could be framed as the “Identification Economy”. Biometric systems accumulate data by turning bodies into machine-readable travel documents. Here, however, the body is the document, or, in David Lyon’s words, it is the passport to space and privilege.14Cp. David Lyon, Surveillance Studies: An Overview, Cambridge, UK, Polity Press, 2007. One could argue that in order to be a productive participant in the theatre of states and corporations today, having an ID, a bank account, or travelling is inextricably tied to “biometric capitalism” and the accumulation and management of data (i.e., people).15Breckenridge shows Galton’s fingerprinting technique for identity registration was an incubator for current systems of biometric citizenship being developed throughout South Africa.
The Making of Suspicious Subjects
As a form of statistical measurement developed at the zenith of Victorian colonialism, biometrics embedded the heritage of eugenicist ideologies. Francis Galton’s thought incorporates the belief that the intelligence and quality of the human race could only be improved by breeding and by cutting away parts of the social organism that were considered to be undesired, unintelligent, or abnormal. In order for Galton to do his research, he needed human bodies. He found his specimens in people perceived as being hard to identify, dangerous, and in need of control. Such groups consisted, for example, of “natives” in the colonies and “hereditary criminals” or paupers in England. The biometric experiments that were first conducted in the colonies are a variation of the “racial calculus and political arithmetic” that was entrenched centuries ago.16Saidiya Hartman, Lose Your Mother: A Journey Along the Atlantic Slave Route, New York, Farrar Straus & Giroux, 2008, quoted from Jonathan Beller, The Message Is Murder. Substrates of Computational Capital, London, Pluto Press, 2017. According to the sociologist Joseph Pugliese, such systems have continuously turned non-white bodies into the necessary suppliers of the material and corporeal substratum: “the lumpen data that has then been converted into higher-order knowledge by the western scientist”.17Joseph Pugliese, Biometrics: Bodies, Technologies, Biopolitics, New York/London, Routledge, 2010, p. 34.
“These non-white bodies have supplied the critical knowledge of the human body that enabled the production of the corporeal cartographies and atlases used in medical schools, academies, forensic laboratories,” Pugliese writes.18Pugliese, Biometrics, p. 34. This early Identification Economy extracted knowledge from bodies in order to satisfy the new scientific disciplines emerging at that time. This, in turn, produced the epistemic legitimisation (the natural racial hierarchy) for colonial extractivism and slavery. From the mid- to late 19th century, this ideology was commonly used to justify the geopolitical competition among empires that wanted to protect their overextended economies.
For the British Empire, biometric fingerprinting emerged as a form of control to stabilise what the historian James Beniger describes as “societal forces unleashed by the Industrial Revolution”.19James Beniger, The Control Revolution: Technological and Economic Origins of the Information Society, Cambridge, MA, Harvard University Press, 1986, p. 7. In this sense, the new discipline of biometrics promised an efficient way for law enforcement to isolate individuals perceived as a threat to the order. In his seminal book The Control Revolution, Beniger argues that control slowly began to shift from bureaucracy to information technology in the mid-20th century. This shift restored, “although with increasing centralization, the economic and political control that was lost at more local levels of society during the Industrial Revolution.”20Ibid., p. 6. Over the course of the 20th century, advancements in computation accelerated the power of state apparatuses and made biometric data much more efficient by gradually linking the body with information technology for control, surveillance, and – in the post-9/11 era – securitisation.21Btihaj Ajana, Governing through Biometrics: The Biopolitics of Identity, London, Palgrave Macmillan, 2013. The 1990s marked a time of transformation. During this period, data was collected for state and corporate intelligence, indicative of a post-Fordist merging of capital and information technology. In the late 90s, John Daugman, Professor of Computer Vision and Pattern Recognition at Cambridge University, patented his automatic iris recognition algorithm, which has since been bought and implemented worldwide by companies and state institutions such as prisons.
Improving the Biometric Machine
Before Galton’s fingerprinting was established as the norm towards the beginning of the 20th century, rival forms of laboratory work and a competition of methods shaped the scientific atmosphere in the burgeoning field of biometrics. Anthropometric police cards gathered in an extensive system developed by Alphonse Bertillon – with each card consisting of a description of physical markers and a mug shot – competed against the so-called Henry Classification System, which included the simple mathematical abstraction embedded in fingerprinting.
As the sociologist Simon Cole suggests, Britain’s decision to adopt the Henry Classification System in 1900 was largely influenced by questions of labour and convenience. In contrast to fingerprinting, the Bertillonage system required too much time, expense, and skilled labour. The promise of (cheaper) unskilled workers, “higher productivity and processing speeds, and the seemingly automatic working of the system” convinced the British Home Secretary Committee to implement the Henry System at Scotland Yard, as Cole describes.22Simon A. Cole, Suspect Identities: A History of Fingerprinting and Criminal Identification, Cambridge, MA, Harvard University Press, 2001, p. 93. Cole states that the “choice of fingerprinting over anthropometry implied a preference for quantity over perceived quality and for industrial-style speed, efficiency, productivity, and economy over what was seen as scientific accuracy and precision.”23Ibid.
Moral Tropes
In order to implement biometrics, subjects and populations must be constructed into categories. This categorisation serves to determine who is suspicious and who is not. Fears about criminality were, for instance, widespread during the Industrial Revolution, as new rail transport enabled an unprecedented amount of migrant workers to circulate in cities. Bertillonage and fingerprinting were presented as effective means of control in the overflowing metropolitan areas of Paris and London. In a certain sense, then, criminals, beggars, and paupers were produced by the Industrial Revolution as a “surplus population”. This population then produced police cards and fingerprints as early datasets for law enforcement. In using the term “surplus population”, I do not intend to put the refugee, pauper, or criminal at the centre of a critique of social exclusion, rendering them as vulnerable victims. On the contrary, I intend to turn this view upside down: without them, there would be no justification for introducing biometrics to control and regulate a quickly growing city. Furthermore, their biometric registration can be understood as a valuable form of living labour.
For some subjects to be safe and secure, others need to be rendered suspicious and dangerous. This maintains the hierarchical divisions of class within the social order. The prominent idea in the 19th century was that crime was hereditary, just as lower and higher characteristics were expressed in a “natural” racial typology. The colonies of the British Empire served as a “laboratory in which criminological theories and techniques were discovered, developed, and tested for eventual application on the common criminal back home”. This mode of governance – in which the hidden existence of a criminal class is exposed through biometric science and technology – spread around the world with the Henry System.24Cole, Suspect Identities, p. 108. The shift towards colonial modes of government in the homeland was linked to a transformation in the relationship between the individual and the state. Now citizens also began to resemble dehumanised colonial subjects: “a mass of strangers, alien, dangerously mobile, and predisposed by heredity to crime, whose identities were batch-processed by the fingerprint system”.25Ibid., p. 96.
This crucial social dynamic reappears today, albeit in a different setting and time. Individuals are classified by supposedly neutral face-detection algorithms calibrated to search categories according to skin tone, hair colour, or facial hair. Skin colour is codified as a default search category based on digital parameters, and is deployed for racial profiling that constructs non-whiteness as an indicator for probabilistic suspicion.26For example, in the decade following 9/11, the New York Police Department made an enormous investment to expand its surveillance apparatus and upgrade its technical capacities. This included a partnership with IBM. As early as 2012, IBM was using its access to vast databases of CCTV footage of New York to test and improve its proprietary Intelligent Video Analytics software, which it later sold to other police departments. Among its innovations, IBM refined tools to search for people captured … Continue reading
By shaping the perception of a constant terrorist threat that can only be countered through data-driven analysis, governments and corporations promote a techno-logic of risk assessment and prediction in which biometrics play an important role. Given the rise of racism, xenophobia, and Islamophobia in American and European politics – alongside ongoing international interventions in conflict zones in the Middle East and Africa – it comes as no surprise that non-white people are systematically subjected to biometric Othering. Within this process, the search category of skin colour becomes normalised, its fabrication and discrimination vanishing beneath the surface of an “objective” interface.
In the recent past, apologists for biometrics have tried to appeal to scientific neutrality and to tie biometrics to the need for securitisation. The terrorist threat after 9/11 became a central point of reference for the industry, as Kelly A. Gates’s reading shows. It was necessary for this industry to erase the history of facial recognition technology in order to secure the authority and desirability of its product.27Kelly A. Gates, “Biometrics and Post-9/11 Technostalgia”, Social Text, 23 (2 (83)), 2005, pp. 35–53, here: p. 49. It can thus be argued that the proclaimed age of global terrorism has in part produced the current expansion of biometric control apparatuses worldwide, similar to how criminals and paupers in Victorian England produced early biometric datasets that then served to stabilise order.
Important moral tropes of the neoliberal era are embedded in crime and migration control and reducing fraud. Since 9/11, claims to reduce fraud and increase efficiency are used in various contexts. One example is the claim that biometrics prevent “fraudulence” in humanitarian work and international aid: digital Doppelgängers who register twice and receive double the amount of refugee benefits.
It is important to see that this default of suspicion and distrust has a function. It enables western policy makers to view whole populations, especially those in and from a region as diverse as the Middle East, as the material upon which risk management strategies must be implemented in the name of counter-terrorism and migration control.
Carceral Logic
From early on, biometric apparatuses had a dual function. On the one hand, they were used to control, punish, and incarcerate criminals and colonial subjects. They were also, however, implemented to disburse early forms of welfare payments, thus keeping the social order in equilibrium. In colonial India, the authorities of the British Empire used biometrics to combat pension fraud, echoing the current justification for biometric scanning in refugee camps. The establishment of the category of suspicion is embedded in the premise of controlling both populations and individuals. Yet the risks of biometric securitisation are, then and now, outsourced to the people. The weak link is the user, never the machine.28See, for instance, DARPA, “Where DARPA is Going, You Don’t Need Password”, DARPA. News and Events. Available at: https://www.darpa.mil/news-events/2013-02-12a [accessed September 2018]. In reality, however, it is the people who feed these biometric machines, who make them work, and give them the appearance of being safe and smart. It is the people who have to endure machinic failures or human-made errors. In an endless loop, it is exactly these people who are disciplined by the very machines they have been forced to help to build.
Beyond simply identifying criminals, biometrics are a lucrative feature within the Prison Industrial Complex. Incarcerated people have often been forced to submit biometric data at times when such practices would not have been accepted outside of prison. The prison has thus been a key laboratory for experimentation.29Joseph Pugliese describes how the torture methods deployed in Abu Ghraib were already practised on African American citizens in domestic prisons in the 1990s. These techniques were later exported to sites such Abu Ghraib or Guantanamo Bay. Joseph Pugliese, State Violence and the Execution of Law: Biopolitical Caesurae of Torture, Black Sites, Drones, New York/London, Routledge, 2013. This situation has escalated drastically over the last decades, as Jackie Wang describes in her book Carceral Capitalism. Wang analyses how mass incarceration is monetised in the US and how a neoliberal, profit-oriented logic drives the management of the prison system, creating a predominantly Black and Hispanic surplus population. Within prisons, these subjects “generate value or are folded into the economy as debtors”.30Jackie Wang, Carceral Capitalism, Semiotext(e) Intervention Series 21, London/Cambridge, MA, MIT Press, 2018, p. 64. This highlights how certain groups that are rendered as surplus populations become the centre of forms of financial extraction by biometric states and global capital.
As Wang notes, the production of a surplus population for extraction is a carceral logic reminiscent of “biometric capitalism”. It produces risky subjects by accumulating data from people who are immobilised as a result of poverty or war. When the allied forces left Iraq in 2011, they left a country in turmoil. Between 2003 and 2011, war and occupation were used as a carceral state of exception to collect fingerprints, iris scans, and DNA from suspected insurgents and civilians. As a result, the Pentagon amassed one of the world’s most comprehensive databases of biometric information ever collected during wartime.
Biometric Divisions
Biometric datasets and borders are growing worldwide. The global biometrics market is expected to reach almost 60 billion dollars by 2025.31Technology Today, 2017 (5), May 2017, p. 2. Within the post-9/11 climate of border and migration securitisation, calculation centres have been established that track subjects classified as risky and suspicious. The body is thus rendered as a site of border politics. Louise Amoore understands biometric borders as a “mobile regulatory site through which people’s everyday lives can be made amenable to intervention and management”. This is, however, only one of many borders “that traverse and inscribe the boundaries of safe/dangerous, civil/uncivil, legitimate traveller/illegal migrant”.32Louise Amoore, “Biometric Borders: Governing Mobilities in the War on Terror”, Political Geography, 25, 2006, pp. 336–351, here: pp. 337–338. New biometric borders along encamped sites enable an invisible form of biopolitical management through dataveillance by states and private corporations. Within the Identification Economy, biometric borders are capital. This capital feeds from living humans and provides intelligence to authorities, thus aiding biopolitical management.33Unknown Author, “Global $40+ Billion Biometric System Market 2018-2023”, PR Newswire, August 13, 2018. Available at: https://www.prnewswire.com/news-releases/global-40-billion-biometric-system-market-2018-2023—-analysis–forecasts-by-by-authentication-type-functionality-component-application-and-geography-300695999.html, [accessed August 2018]. Edward Said’s statement at the beginning of this essay points to the idea of generalisation. On a level of biopolitical generality, biometric bodies and the data they produce become nodes in a giant transnational network that exists in colonial continuity, extracting value from former colonies.
Classification is itself a practice of building borders within the social order. It fragments human bodies into parts, prints, and statistical outputs that subsequently enable new arrangements and schemes, much like the division of labour so crucial to the Industrial Age. The dis- and reassembling of labour accelerated the evolution of productive forces. Similarly, the production of types of people, movements, and behaviours enables the extraction of data from a surplus population. Embedded categories such as race, class, gender, disability, and age order people into segmented groups within a population. In presenting the social order as natural, biometric systems maintain the race, gender, and class (b)orders within states.
Biometric Labo(u)ratories

We return to Fallujah in Iraq, a site of what can be framed as biometric labour executed by force. The first biometric tests were conducted during the siege in 2004, when the city served as a laboratory for population management under a state of exception.34Benjamin Muller and John Measor, “Securitizing the Global Norm of Identity Biometrics and Homo Sacer in Fallujah”, in Benjamin Muller (ed.), Security, Risk and the Biometric State, London/New York, Routledge, 2010, pp. 102–117, here: p. 103. All men between the ages of 15 and 45 were regarded as suspicious figures and potential terrorists. Biometric systems were presented as a simple way to identify friend or foe, creating a high-tech net “to keep ‘em from swimming freely.”35Shachtmann, “Iraq Diary”.
The laboratory of war served to strengthen the biometric machine. Iraqi citizens can thus be called the testers and improvers of biometric population management. Their data was, however, extracted by force. This points to the invisible layers of forced labour that are needed for the biometric control apparatus to work properly. Currently, the US military runs a biometrics lab in an undisclosed area in Iraq to test biometrically enabled “multi-modal access control systems”.36Chris Burt, “U.S. Army deploys contactless multi-modal access control system to Iraq”, Biometrics Research Group, February 27, 2018. Available at: https://www.biometricupdate.com/201802/u-s-army-deploys-contactless-multi-modal-access-control-system-to-iraq [accessed October 31, 2019]. Similar to the UN Refugee Agency (UNHCR), they have started to feed massive amounts of information into neural networks in order to predict behaviour, movement, and migration through pattern recognition. Furthermore, the US has begun to test a remote, contact-free form of data collection that doesn’t interrupt traffic at checkpoints, recalling a cybernetic factory that accumulates data and produces control.
Accumulated Collective Intelligence
The future of the West is tested, cultivated, and stabilised in distant laboratories like refugee camps or “Camp Fallujah”. In this process, it becomes marketable. The integration of evermore corporeal traits and behavioural biometrics into these systems recalls the complex assemblage of apparatuses Alphonse Bertillon used for measurement almost 150 years ago. Bertillon’s vision may indeed return, newly equipped with procedures involving solid computational statistics and made robust through experimentation. States and corporations continue to use Iraqi territories and bodies to test and improve their product. This transfer of commodities and information is a hidden history of experimentation, dispossession, and accumulation.37For the term “hidden history of experimentation” see again Jacobsen, “Making Design Safe for Citizens”. Biometric dataveillance entails a massive accumulation of data. It merges with global capital in corporations such as Accenture or SAP, who provide management software, or Aware, a global provider of biometrics software and hardware. Such corporations manage and analyse data for the military, states, transnational institutions like the UN Refugee Agency, and, of course, the private sector. Since the data points are, however, the people themselves, it is their collective, accumulated intelligence that keeps these biometric machines running.38See also Pasquinelli, “Italian Operaismo and the Information Machine”. Because the corporate and military race for biometrics markets has also been a race for the possession and management of data banks, a central question to ask is: who has accumulated this data, who owns it, and who owns the data-bank?
Tableau Imaginaries
In Iraq and Afghanistan, forensic technologies were to a large extent implemented alongside biometrics. In 2012, the Defense Forensics and Biometrics Agency (DFBA) was established, expanding the territory of the battlefield. Biometric control still applies the idea of network-centric warfare, a post-Cold War strategy developed in the 1990s. This method uses control and command information technology to achieve battlefield dominance in real-time. Biometric systems centred around the control of movement in and beyond the battlefield employ this same idea. That is to say, these systems work to achieve identity dominance through networked information technology in real-time.

Identity is the Name of a Battlefield
The large datasets produced by science and law enforcement at the turn of 19th century form the material backbone and precedent to current machine learning datasets. This backbone continues to grow thanks to the production of data accumulated by an informal and invisibilised workforce of surplus populations. Bodies are measured in a networked factory in which biometric data is captured as living labour. In this sense, the product is a form of intelligence that acts back upon citizens as control and surveillance. Its sites of production are places of experimentation and violence, accumulation and dispossession; where surplus value is produced through new enclosures and extractivism.40Sandro Mezzadra and Brett Neilson, The Politics of Operations: Excavating Contemporary Capitalism, Durham, Duke University Press, 2019. Within these sites, a precarious and involuntary new form of data production takes place. Here machines are trained and tested for further dataveillance in developed countries. Biometric applications are transferred to the West as products of these “hidden histories of experimentation”, for instance in the form of biometric clocks or wearable devices that measure (and control) productivity.
As a strategy of governance, classification first produced new subjects to then render them guilty, manageable, or in need of management. Biometrics enabled an epistemic production of connected subjects of (in)security. This laid the foundation for today’s computational state and corporate intelligence. As a consequence, biometric and algorithmic governance is normalised, often hiding behind the buzzword of an almost mythical sapient “Artificial Intelligence” which, in reality, is part of computational state and corporate models that capture daily movements on a planetary scale. While it absorbs data from refugee camps, “Camp Fallujah”, and other peripheral sites of exception (from the viewpoint of western hegemony), the output, data, databanks and intelligence remain in the hands of military and commercial industries.
In his unpublished novel Kantsaywhere, Francis Galton introduces a eugenically optimised society that functions like an engineered community within a laboratory. It is his personal utopia in which people of inferior stock are sentenced to debt, celibacy, or labour camps, and upward mobility is only possible through examination by a college that assesses fitness and intelligence. This is perhaps the clearest application of Social Darwinism.41Charles Darwin was Francis Galton’s half-cousin. Galton’s utopia points to a vision for a biodata-driven governance; one in which information, intelligence, and “scientific” measurement oscillate around capitalised surplus population management. This makes at least two things clear: that capital, after Marx, is a social relation and that in these relations, an antagonism comes to light between those who create and those who accumulate and appropriate.
| ↑1 | Edward Said, Orientalism, New York, Vintage Books, 1979, p. 86. |
|---|---|
| ↑2 | Keith Breckenridge, Biometric State: The Global Politics of Identification and Surveillance in South Africa. 1850 to the Present, Cambridge, Cambridge University Press, 2014, p. 9. |
| ↑3 | John D. Woodward, Jr., “Using biometrics to achieve identity dominance in the Global War on Terrorism”, Military Review, September/October 2005, pp. 30–34. |
| ↑4 | Noah Shachtmann, “Iraq Diary: Fallujah’s Biometric Gates”, Wired, August 31, 2007. Available at: https://www.wired.com/2007/08/fallujah-pics/ [accessed September 2018]. |
| ↑5 | Cp. Allan Sekula, “The Body and the Archive”, October, 39, 1986, pp. 3-64. |
| ↑6 | I borrow the term “hidden history of experimentation” from Katja Lindskov Jacobsen, “Making Design Safe for Citizens: A Hidden History of Humanitarian Experimentation”, Citizenship Studies, 14 (1), 2010, pp. 89-103. |
| ↑7 | Social labour and collective intelligence are used to emphasize an approach that understands biometrics as a socio-material assemblage and looks at its collective and social dimension in the sphere of production. This essay will foreground the fact that Iraqi citizens as collective producers were needed to animate and improve the biometric apparatus; with Fallujah as the site for data extraction. See also Matteo Pasquinelli, “Italian Operaismo and the Information Machine”, Theory, Culture & Society, 32 (3), 2015, pp. 49–68. |
| ↑8 | Cp. Francis Galton, Finger Prints, London/New York, Macmillan & Co, 1982, p. 2. |
| ↑9 | Keith Breckenridge, Biometric State, p. 29. |
| ↑10 | Cp. Francis Galton Finger Prints. |
| ↑11 | Hito Steyerl in Conversation with Marvin Jordan, “Hito Steyerl. Politics of Post-Representation”, Dismagazine. Discover, n.d. Available at: http://dismagazine.com/disillusioned-2/62143/hito-steyerl-politics-of-post-representation [accessed August 27, 2018]. |
| ↑12 | Harun Farocki, A Way, 2005, https://www.harunfarocki.de/installations/2000s/2005/a-way.html, accessed August 31, 2018. |
| ↑13 | In Nigeria, for instance, Mastercard has issued national biometric ID cards that people can also use to pay and vote. |
| ↑14 | Cp. David Lyon, Surveillance Studies: An Overview, Cambridge, UK, Polity Press, 2007. |
| ↑15 | Breckenridge shows Galton’s fingerprinting technique for identity registration was an incubator for current systems of biometric citizenship being developed throughout South Africa. |
| ↑16 | Saidiya Hartman, Lose Your Mother: A Journey Along the Atlantic Slave Route, New York, Farrar Straus & Giroux, 2008, quoted from Jonathan Beller, The Message Is Murder. Substrates of Computational Capital, London, Pluto Press, 2017. |
| ↑17 | Joseph Pugliese, Biometrics: Bodies, Technologies, Biopolitics, New York/London, Routledge, 2010, p. 34. |
| ↑18 | Pugliese, Biometrics, p. 34. |
| ↑19 | James Beniger, The Control Revolution: Technological and Economic Origins of the Information Society, Cambridge, MA, Harvard University Press, 1986, p. 7. |
| ↑20 | Ibid., p. 6. |
| ↑21 | Btihaj Ajana, Governing through Biometrics: The Biopolitics of Identity, London, Palgrave Macmillan, 2013. |
| ↑22 | Simon A. Cole, Suspect Identities: A History of Fingerprinting and Criminal Identification, Cambridge, MA, Harvard University Press, 2001, p. 93. |
| ↑23 | Ibid. |
| ↑24 | Cole, Suspect Identities, p. 108. |
| ↑25 | Ibid., p. 96. |
| ↑26 | For example, in the decade following 9/11, the New York Police Department made an enormous investment to expand its surveillance apparatus and upgrade its technical capacities. This included a partnership with IBM. As early as 2012, IBM was using its access to vast databases of CCTV footage of New York to test and improve its proprietary Intelligent Video Analytics software, which it later sold to other police departments. Among its innovations, IBM refined tools to search for people captured in video streams according to skin tone, hair colour, or facial hair. |
| ↑27 | Kelly A. Gates, “Biometrics and Post-9/11 Technostalgia”, Social Text, 23 (2 (83)), 2005, pp. 35–53, here: p. 49. |
| ↑28 | See, for instance, DARPA, “Where DARPA is Going, You Don’t Need Password”, DARPA. News and Events. Available at: https://www.darpa.mil/news-events/2013-02-12a [accessed September 2018]. |
| ↑29 | Joseph Pugliese describes how the torture methods deployed in Abu Ghraib were already practised on African American citizens in domestic prisons in the 1990s. These techniques were later exported to sites such Abu Ghraib or Guantanamo Bay. Joseph Pugliese, State Violence and the Execution of Law: Biopolitical Caesurae of Torture, Black Sites, Drones, New York/London, Routledge, 2013. |
| ↑30 | Jackie Wang, Carceral Capitalism, Semiotext(e) Intervention Series 21, London/Cambridge, MA, MIT Press, 2018, p. 64. |
| ↑31 | Technology Today, 2017 (5), May 2017, p. 2. |
| ↑32 | Louise Amoore, “Biometric Borders: Governing Mobilities in the War on Terror”, Political Geography, 25, 2006, pp. 336–351, here: pp. 337–338. |
| ↑33 | Unknown Author, “Global $40+ Billion Biometric System Market 2018-2023”, PR Newswire, August 13, 2018. Available at: https://www.prnewswire.com/news-releases/global-40-billion-biometric-system-market-2018-2023—-analysis–forecasts-by-by-authentication-type-functionality-component-application-and-geography-300695999.html, [accessed August 2018]. |
| ↑34 | Benjamin Muller and John Measor, “Securitizing the Global Norm of Identity Biometrics and Homo Sacer in Fallujah”, in Benjamin Muller (ed.), Security, Risk and the Biometric State, London/New York, Routledge, 2010, pp. 102–117, here: p. 103. |
| ↑35 | Shachtmann, “Iraq Diary”. |
| ↑36 | Chris Burt, “U.S. Army deploys contactless multi-modal access control system to Iraq”, Biometrics Research Group, February 27, 2018. Available at: https://www.biometricupdate.com/201802/u-s-army-deploys-contactless-multi-modal-access-control-system-to-iraq [accessed October 31, 2019]. |
| ↑37 | For the term “hidden history of experimentation” see again Jacobsen, “Making Design Safe for Citizens”. |
| ↑38 | See also Pasquinelli, “Italian Operaismo and the Information Machine”. |
| ↑39 | Cp. Defense Forensics & Biometrics Agency, Official Website, 2019. Available at: https://www.dfba.mil/, [accessed August 2018]. |
| ↑40 | Sandro Mezzadra and Brett Neilson, The Politics of Operations: Excavating Contemporary Capitalism, Durham, Duke University Press, 2019. |
| ↑41 | Charles Darwin was Francis Galton’s half-cousin. |
Ariana Dongus is a media scholar, journalist and teacher based in Berlin and Karlsruhe. In exploring the intersection of biometrics, colonial pasts, new forms of work, and machine intelligence, she contributes to a critique of today’s digital economies. Her recent publications include journalistic reports and essays. She is a PhD candidate at Hochschule für Gestaltung Karlsruhe where she also works as a lecturer. At HfG, she coordinates KIM, a research group for critical studies in machine intelligence.
